Information Security
Information technology security is a relevant task of numerous organizations with automated business processes. The organization activity is always under the threat, whether these are accidental threats or intended situations. Their occurrence can cause damages to organizations and let achievement of goals down.
High information system security increases trust from clients' and partners' parties, and often this is one of the bases for the company success.
Open Technologies offers effective solutions in the field of information security:
- Information Security Management Systems
- Security Information Management
- Basic IS Systems (firewalls, VPN, IPS)
- Internet Access Protection
- Analytical IS Systems
- IS Systems Complying to Regulatory Requirements
The solutions on information security offered by our company will help:
- to protect all forms of information against leakage threats, unauthorized modification and loss;
- to ensure absence of unacceptable damage caused by IS incidents;
- to ensure IT systems operation according to requirements;
- to comply to requirements of legislative and regulatory documents;
- to ensure growth of trust from the clients' and partners' parties.
- to ensure fault-tolerance, accounting and authenticity of operations in information systems;
- to optimize expenses of IS assurance in organization.
The main principle we base on in information security assurance consists in the idea that IS assurance shall be based on organization-wide complex and system foundation by creation of information security system (ISS). ISS is a complex of technical, organizational and legal measures. The figure displays main elements which can be included into ISS:
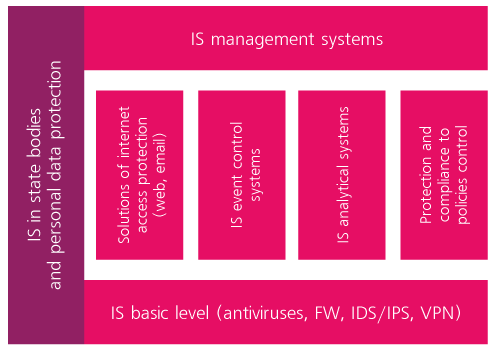
Methodology of IS control is based on approaches stipulated by the international ISO/IEC 27001:2005 standard. This standard describes the general principles of construction and requirements to information security management systems (ISMS) and includes PDCA (Plan-Do-Check-Act) control cycle aspects, risk management and the best practices of the IS assurance.
This ISS approach provides the customers with the following advantages:
- possibility to organize effective and economically viable solution of the general IS assurance tasks according to requirements;
- possibility of individual support and improvement of IS assurance in case of changes in IT infrastructure, business-processes, legislation requirements, relevant threats and vulnerabilities;
- compliance to requirements of provisions on sufficient capital known and Basel II agreement;
- possibility to demonstrate compliance to requirements of legislative and regulatory documents, both Russian (standard of the Bank of Russia, Law "On personal data", RD FSTEC, etc.) and international ones (Sarbanes-Oxley Act, Gramm-Leach-Bliley Act which is relevant for companies working at the Western markets);
- official certification to compliance to ISO/IEC 27001:2005 in order to provide quality confirmations.
ISS construction and certificates of its quality allows provision of substantiated warranties to owners, business partners, investors and clients that the IS task is duly solved in the organization. In its turn, this ensures the organization competitive advantages demonstrating competence in IS threat control which are the main part of all operation risks.
Open Technologies accumulated vast experience in designing and introduction of information security solutions. Our customers include largest Russian and international enterprises and organizations.
Open Technologies has all necessary intellectual and industrial recourses to solve complex tasks of information security system construction. Our service package includes pre-design inspection, system development and design, integration and interfacing with existing information infrastructure, installation and execution of acceptance tests as well as service and technical support, providing optimal and continuous work of the system.








